
How to Prevent the Desjardins Security Breach
In 2019, Desjardins Bank disclosed that they had been subject to a large internal security breach. One of their employees had collected the personal information of some 2.7 million customers and had shared that information with a third party outside of the financial institution. The fallout for the company was enormous. The breach attracted ongoing press coverage and piqued the interest of the Canadian House of Commons. The Desjardins executive team was consumed with mitigating the security and reputational damage. This internal breach resulted in a costly and resource-heavy distraction from their normal course of business.
Protection from Internal Threats
The Desjardins security breach provides an example of the internal threats facing organizations. Internal threats are very real and need to be taken seriously. However, most of our clients do not express much interest in protecting themselves from internal vulnerabilities. If we approach them to do internal monitoring or to create internal controls, we often get a lot of pushback. It is understandable. Organizations trust their teams and would prefer to devote their resources towards protecting themselves from unknown external bad actors. At the same time, most organizations have zero experience trying to do risk mitigation around internal vulnerabilities.
Most of our clients do not express much interest in protecting themselves from internal threats. If we approach them to do internal monitoring or to create internal controls, we get a lot of pushback.
How to Prevent the Desjardins Security Breach
- Data Structures and Data Loss Prevention (DLP)
- File System Resource Management (FSRM)
- Automated Data Loss Prevention Tools
- What could have prevented the Desjardins breach?
The Desjardins example is about data loss. We protect against this type of security breach with our data loss prevention (DLP) services. The most fundamental tenet of DLP is to carefully control who has access to data. In order to control access, an organization must implement a policy of minimal required access.
Minimal Required Access
Minimal required access means that employees who do not need access to the data for their jobs, should not have access to that data.
From the information available in the mainstream media, it is not clear to CITI whether this ex-employee had legitimate access to information, or if Desjardins Bank had minimal required access controls in place.
It is possible that the Desjardins security breach was for profit. Someone has been arrested. A class action suit has commenced and there may be more civil litigation. Perhaps the Desjardins Bank situation was like the Edward Snowdon situation, where access to data was typical and widespread.
It is possible that the doctrine of minimal required access was not implemented or maintained. Desjardins Bank might be too embarrassed to admit that there were major gaps in their internal security measures. It is also possible that the employee sought to inflict reputational damage. Whatever the reasons behind the Desjardins security breach, the implementation of the doctrine of minimal required access could have prevented the breach and definitely would have mitigated the resultant damages. Other tools and tactics that might have prevented the Desjardins situation include:
- Attention to data structures and data loss prevention (DLP)
- File system resource management (FSRM)
- Automated data loss prevention tools
1. Data Structures and Data Loss Prevention (DLP)
At CITI, we focus on all elements of operational security. If Desjardins Bank had come to us to implement a risk mitigation protocol, we would have started with a comprehensive data access review. This includes looking at applications like software—who has access and at what level—as well as more mundane operations, such as who has access to existing files on a file share platform. Often people who once needed access to data to perform their jobs still have access when they no longer need it.
Data Structures
Currently, there are no widely followed best practices for data structures. In other words, there is no single best way to set up data folders and as a result most organizations create data storage structures on an ad hoc basis. Over the course of time, that can make things inconsistent between departments and operational units. Unless your data is structured in a consistent and logical manner, it is very difficult to control data access.
An example, of a well-ordered file system might look like this HR departmental shares folder. Within the department, it might be organized by primary areas of responsibility. Within each area there is a more granular expansion of the job function.
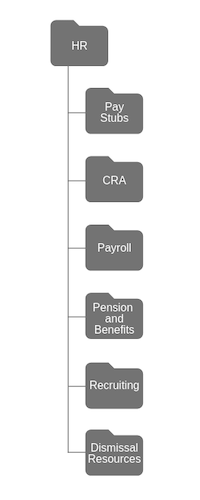
As mentioned above, because there are so many different ways of organizing data, organizations arrange their data on an ad hoc basis. They allow users to create folders in common spaces and these extra folders present as dangerous security gaps. Once you have structured data carefully, it permits you to implement access control systems that allow minimum required access.
Organizations often do not think about the implications of allowing access. For example, a director of HR and senior HR manager might be doing a project to review executive compensation. Between them, they will create a number of different files. At a minimum, they will create new files inside HR and payroll. They assume the data is safe without necessarily recognizing that everyone in the HR department is allowed to look at the HR folder. Executive compensation data should be restricted and accessed only by people dealing with payroll but now an entire department has access to information that they do not need. There is now widely available data on all of the bonuses that were issued. Maybe some are surprised at this data and think it is not fair or think that they can offer the bonuses to all new hires. That situation is referred to as a data loss security breach.
Subfolders
Data loss security prevention protocols mandate that you should not set up a subfolder until you know who owns the folder. Following this basic matter-of-fact operational policy of minimum required access would require the HR department to create a list of everyone (down to the lowest level clerk) who has potential access to that data. Reviewing and auditing file folder access is important and by necessity, ongoing.
Desjardins Bank did not lose their data, but rather, they lost control of it.
2. File System Resource Management (FSRM)
Another security system that can be implemented is File System Resource Management, or FSRM. It is a system that logs when every single file is accessed—who accessed it, when they opened it, if they modified it, and where they saved it. An FSRM can immediately tell you about everyone who touches the data in any manner.
We implemented an FSRM system for our client, Nanowave Technologies. It generated 30 TB of data in one year. You need massive computers and AI to review that data because it is important to be able to analyze patterns. For example, if a pattern of activity was breached by someone reaching outside the systems, the FSRM would flag the IT department and would send an email to a manager saying that a person accessed a folder outside of the normal established patterns.
Very sophisticated tools are required for an FSRM and you also need to have established internal processes, including a periodic review schedule. You also need well-defined escalation procedures. Who has access to what and when? Remember: Desjardins Bank did not lose their data, but rather, they lost control of it. A key dilemma that organizations must address is the unauthorized sharing of information.
3. Automated Data Loss Prevention Tools
Given that most organizations are highly porous entities, how can you really keep an eye on all those revolving doors? The short answer is: creating an FSRM along with monitoring and escalation procedures. Escalation procedures are put in place to handle potential issues in a variety of situations. In a call centre, for example, an escalation plan specifies measures to be implemented when unexpected strain or an increased level of stress is placed upon the centre. These are important practices, policies and procedures, but very few organizations have them in place.
Automated data loss prevention tools can monitor the content of email and who the emails are being sent to. A disgruntled employee may have started to delete their email. Without a historical record, a forensic discovery effort can sometimes cost more than the damages in a lawsuit.
Automated tools recognize what people typically do in their jobs and identifies a pattern of usage of data and systems. Anything outside of this pattern would show up as a red flag. For example, an email to .nk or .ru would be flagged, as the system knows that staff do not send messages to North Korea or Russia.
Content monitoring systems can also be employed. These monitoring systems prevent people from going to certain sites from their work device or during work hours.
4. What could have prevented the Desjardins Bank breach?
In all likelihood one of two things happened that led to the Desjardins' security breach:
- An individual had access to data that they should not have had, or
- Desjardins Bank implemented a legitimate and secure file-sharing protocol but the employee went rogue
Often when organizations are in the throws of a security breach or a privacy breach they are very embarrassed and things are chaotic. In the event of a security breach the public often sees the company as a victim. The opposite is true of privacy breaches which often make the public question the competence of the organization. While both are bad, privacy breaches present huge accountability questions to management and IT.
If Desjardins Bank were a CITI customer, we would offer to set up a minimal required access protocol. We would start with the basics:
- Exactly who has access to which folders or files? This means that you do not trust anybody with anymore than you need to trust them with.
- Not only should the data be protected from outside sources but some data, such as compensation should not be readily available to inside sources either.
Once minimal required access protocols were established, we would implement universal data structures and discuss file system resource management and automated data loss prevention tools.
What happened to Desjardins Bank is a corporate nightmare but it can get even worse if the hackers do something with the ill-gotten data. Data loss security planning is essential for all organizations and will help you sleep at night.
To safeguard your organization from an internal security breach, get in touch with CITI. We will look at how your data is structured and implement minimum required access, along with other data loss prevention tools.
Feature image copyright CBC.ca.
 |
 |






